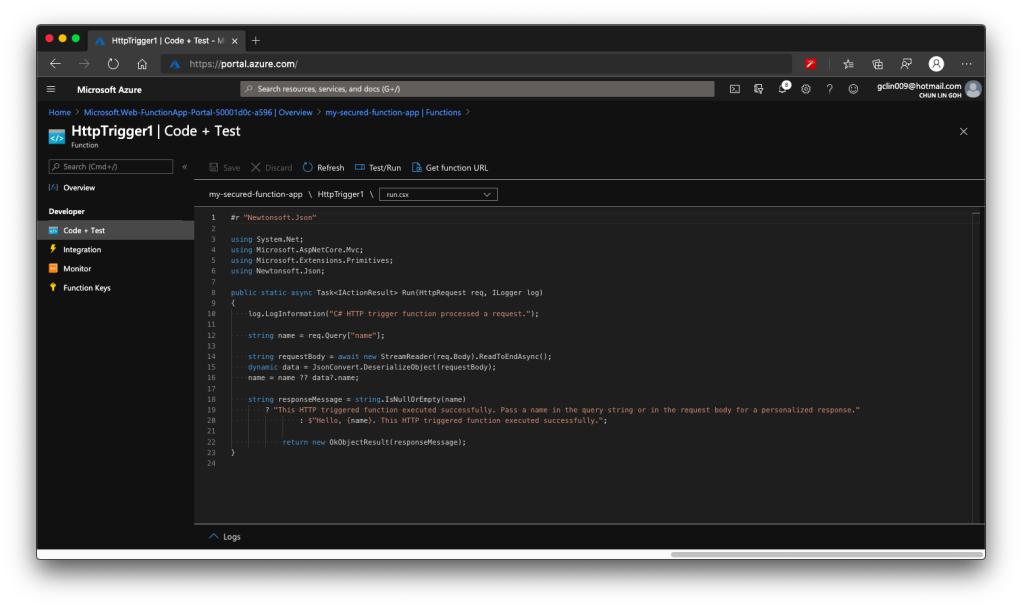
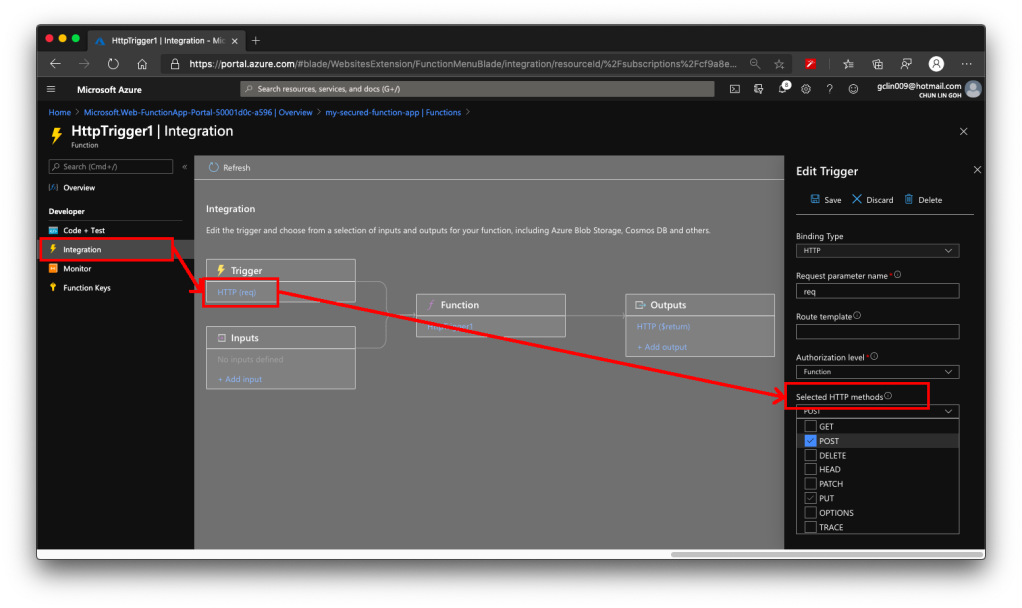
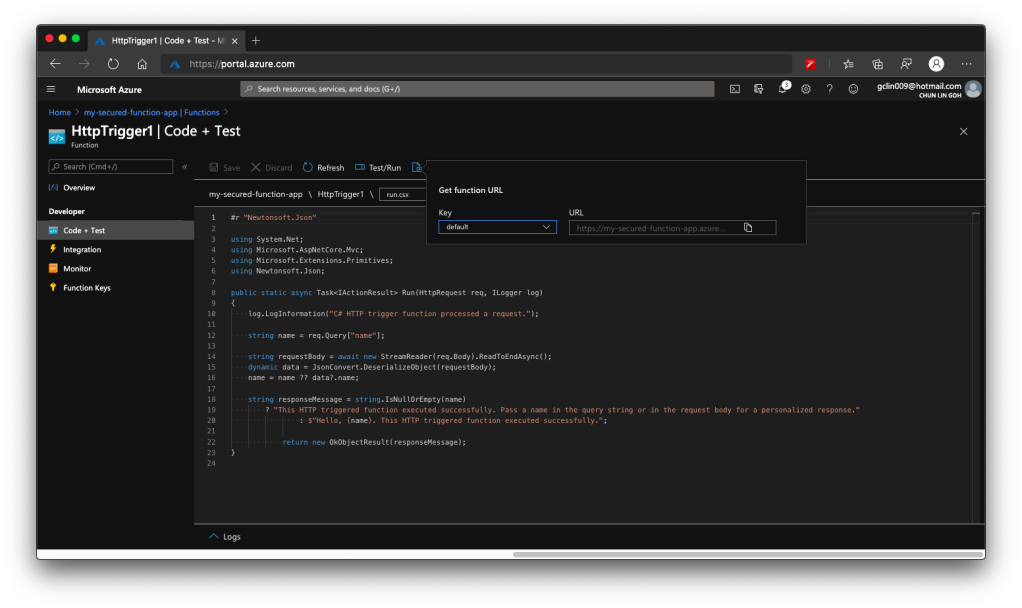
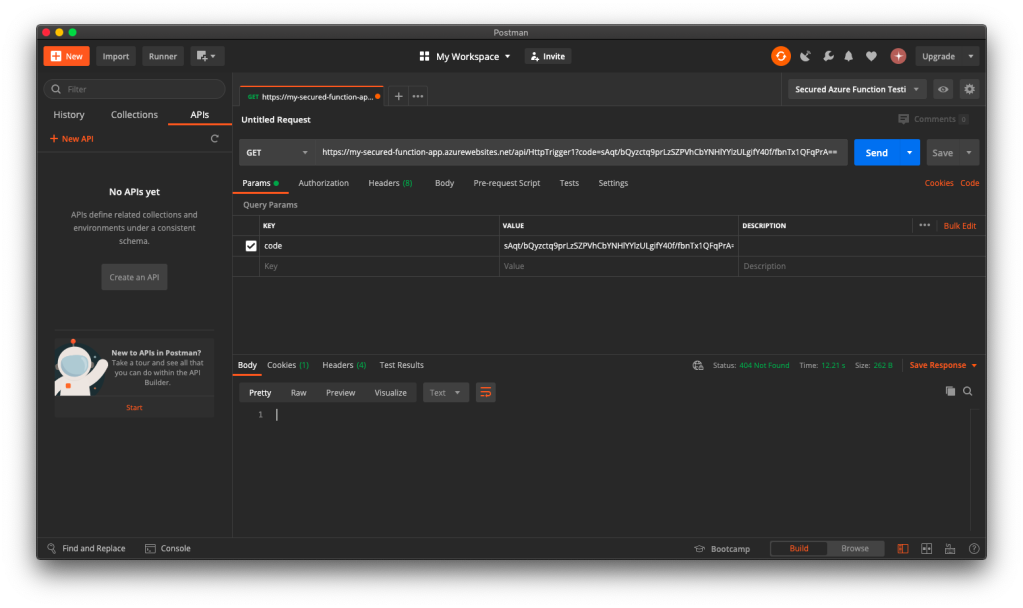
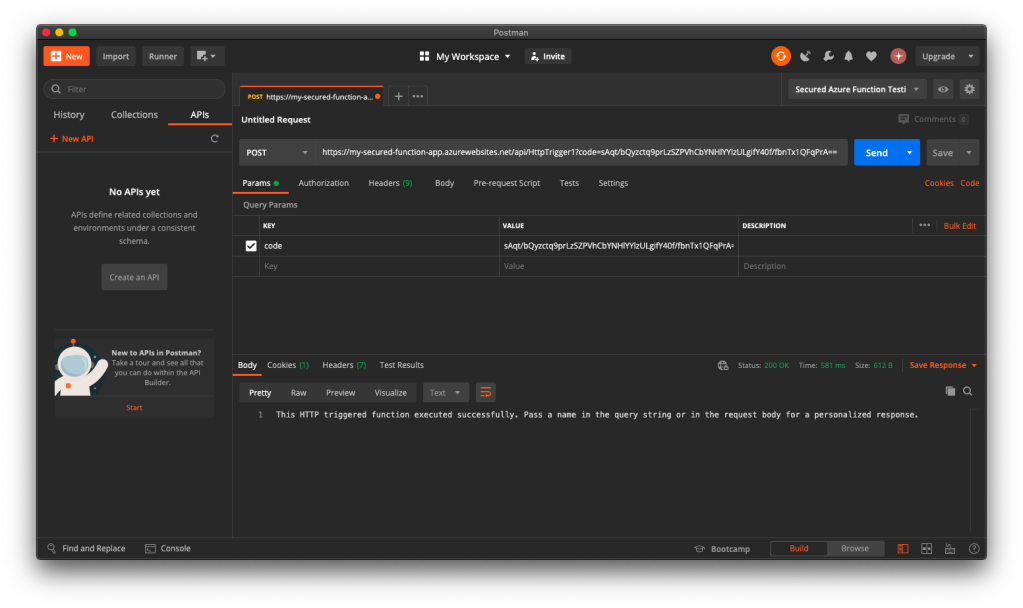
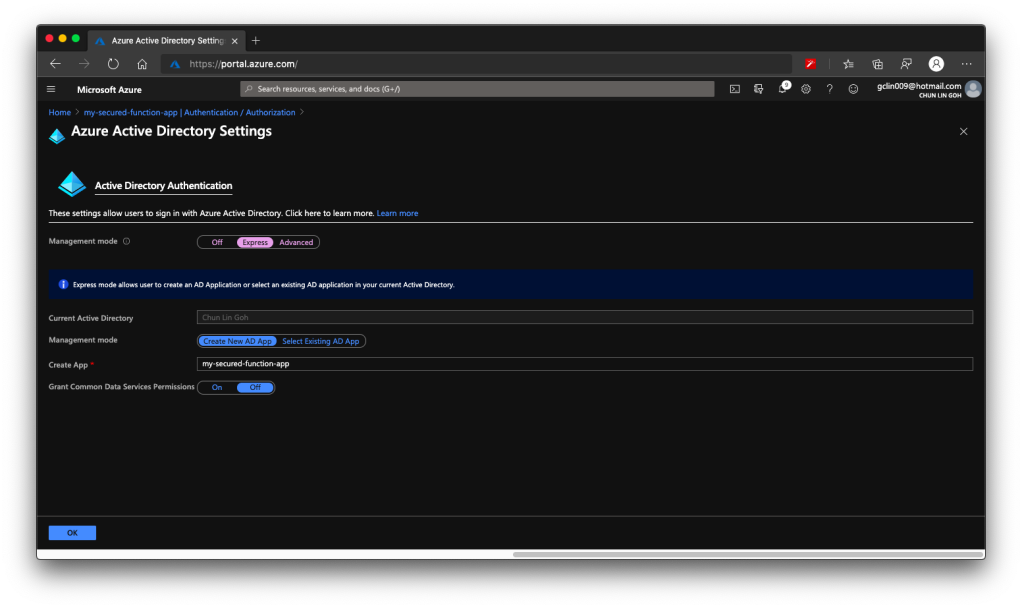
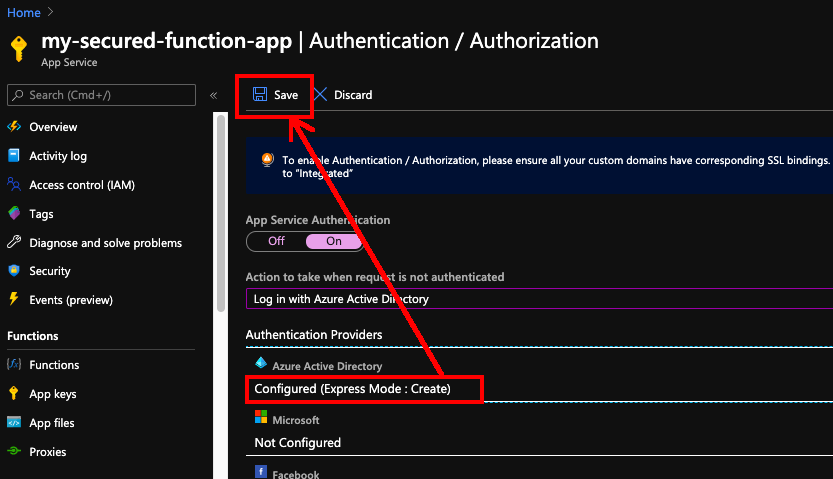
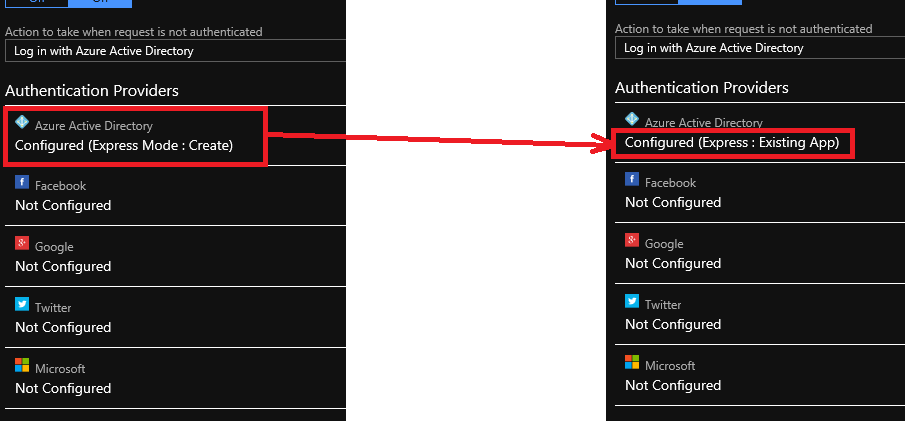
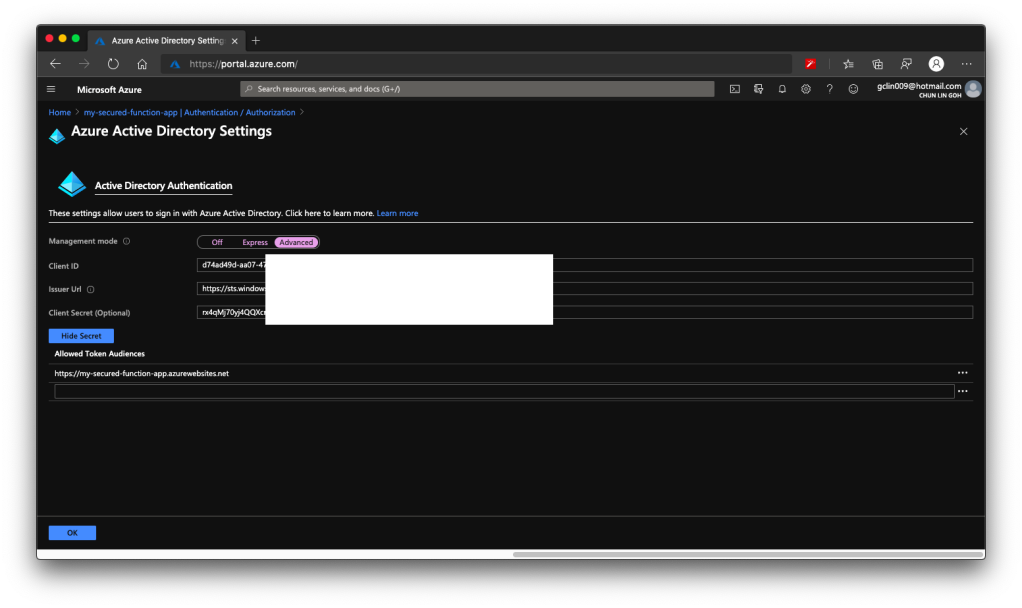
For API developers, Postman is a popular tool that streamlines the process of testing APIs. Postman is like having a Swiss Army knife for API development as it allows developers to interact with APIs efficiently.
In March 2023, Postman Flows was officially announced. Postman Flows is a no-code visual tool within the Postman platform designed to help us create API workflows by dragging and dropping components, making it easier to build complex sequences of API calls without writing extensive code.
Recently, my teammate demonstrated how Postman Flows works, and I’d like to share what I’ve learned from him in this article.
Use Case
Assume that there is a list of APIs that we need to call in sequence every time, then we can make use of Postman Flows. For demonstration purpose, let’s say we have to call the following three AWS APIs for a new user registration.
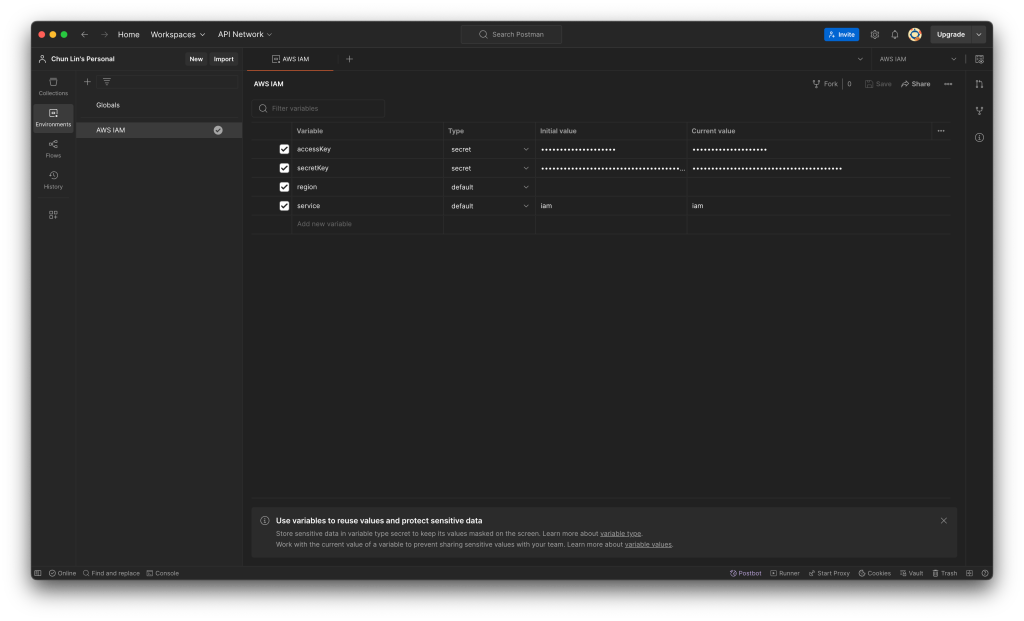
We will first need to define the environment variables, as shown in the following screenshot.
Next, we will setup the three API calls. For example, to create a new user on AWS, we need to make an HTTP GET request to the IAM base URL with CreateUser as the action, as shown in the following screenshot.
To tag the user, for example assigning the user above to a team in the organisation, we can do so by setting TagUser as the action, as shown in the screenshot below. The team that the user will be assigned to is based on their employee ID, which we will discuss later in this article.
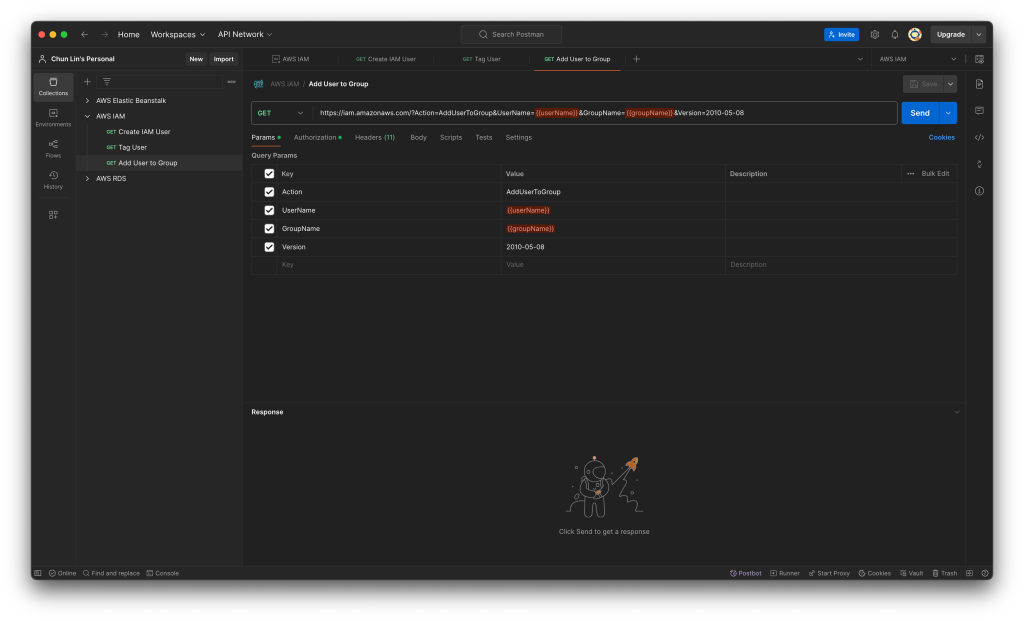
Finally, we will assign the user to an existing user group by setting AddUserToGroup as its action.
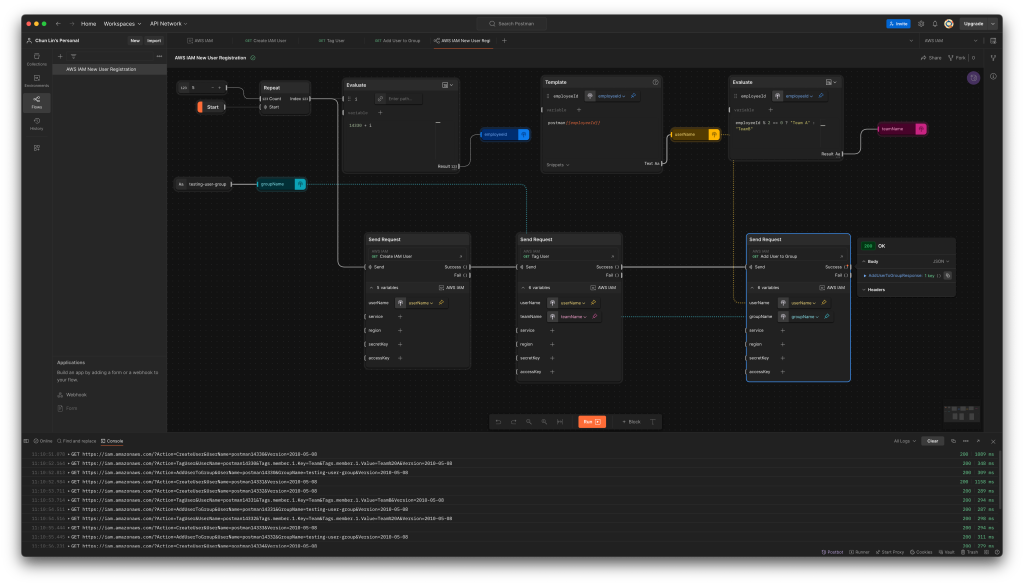
Create the Flow
As demonstrated in the previous section, calling the three APIs sequentially is straightforward. However, managing variables carefully to avoid input errors can be challenging. Postman Flows allows us to automate these API calls efficiently. By setting up the Flow, we can execute all the API requests with just a few clicks, reducing the risk of mistakes and saving time.
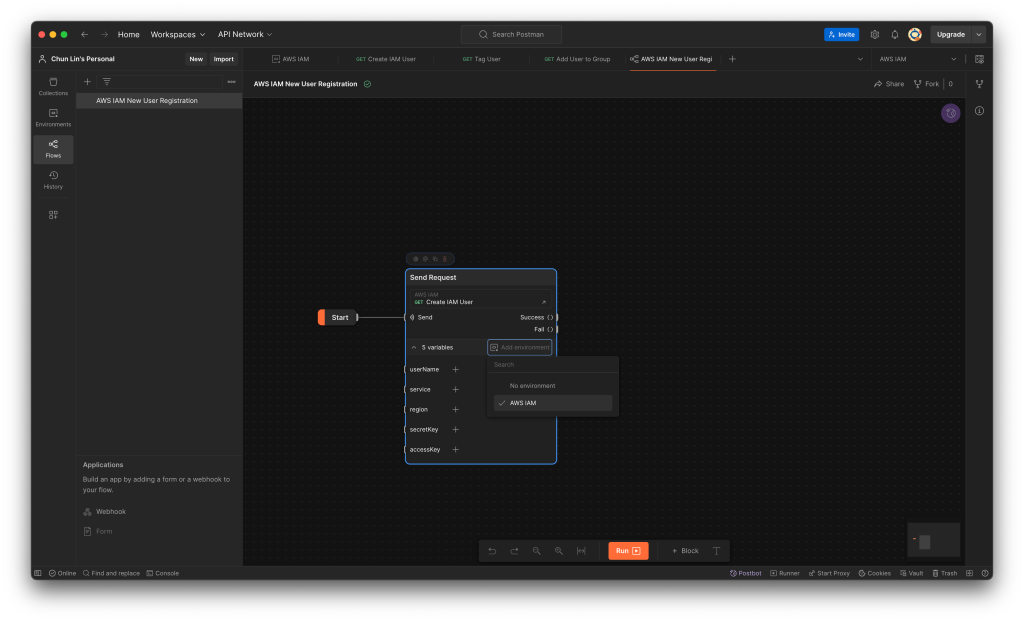
Firstly, we will create a new Flow called “AWS IAM New User Registration”, as shown below.
By default, it comes with three options that we can get started. We will go with the “Send a request” since we will be sending a HTTP GET request to create a user in IAM. As shown in the following screenshot, a list of variables that we defined earlier will be available. We only need to make sure that we choose a correct Environment. The values of service, region, accessKey, and secretKey will then be retrieved from the selected Environment.
Since the variable userName will be used in all three API calls, let’s create a variable block and assign it a value called “postman03”.
Next, we simply need to tell the API calling block to assign the value of userName to the field userName.
Now if we proceed to click on the “Run” button, by right, the call should respond with HTTP 200 and relevant info returned from AWS, as demonstrated below.
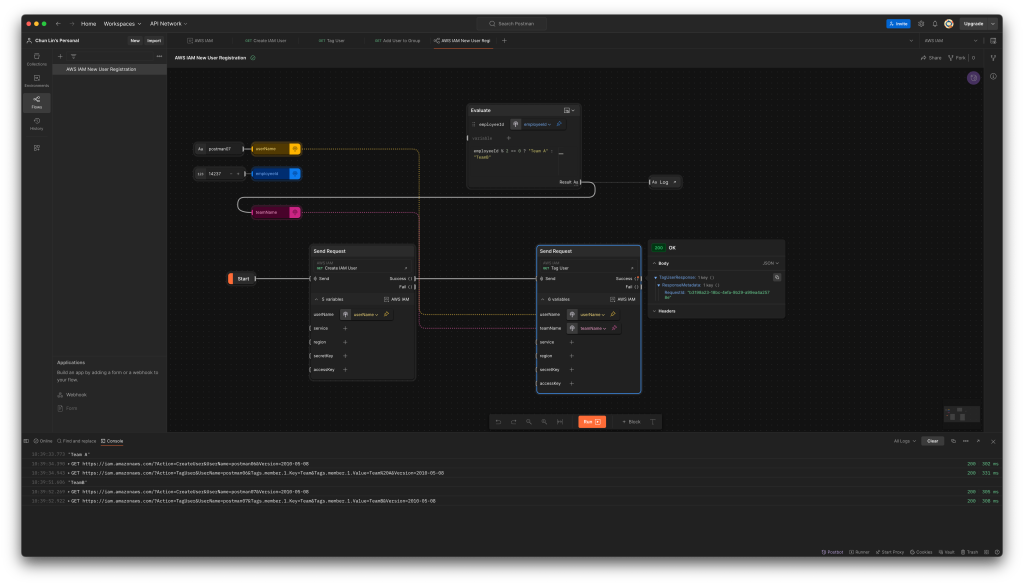
With the success of user creation, the next step is to call the user tagging API. In this API, we will have two variables, i.e. userName and teamName. Let’s assume that the teamName is assigned based on whether the user’s employeeId is an even or odd number, we can design the Flow as shown in the following screenshot.
As shown in the Log, when we assign an even number to the user postman06, the team name assigned to it is “Team A”. However, when we assign an odd number to another user postman07, its team name is “Team B”.
Finally, we can complete the Flow with the third API call as shown below.
Now, we can visit AWS Console to verify that the new user postman09 is indeed assigned to the testing-user-group.
The Flow above only can create one new user in every Flow execution. By using the Repeat block which takes a numeric input N and iterates over it from 0 to N - 1, we can create multiple users in a single run, as shown in the following updated Flow.
Variable Limitation in Flows
Could we save the response in a variable that allows us to reuse its value in other Flow? We would guess this is possible with variables in Postman.
Postman supports variables at different scopes, in order from broadest to narrowest, these scopes are: global, collection, environment, data, and local.
The variable with the broadest scope in Postman is the global variables which are available throughout a workspace. So what we can do is actually storing the response in the global variables.
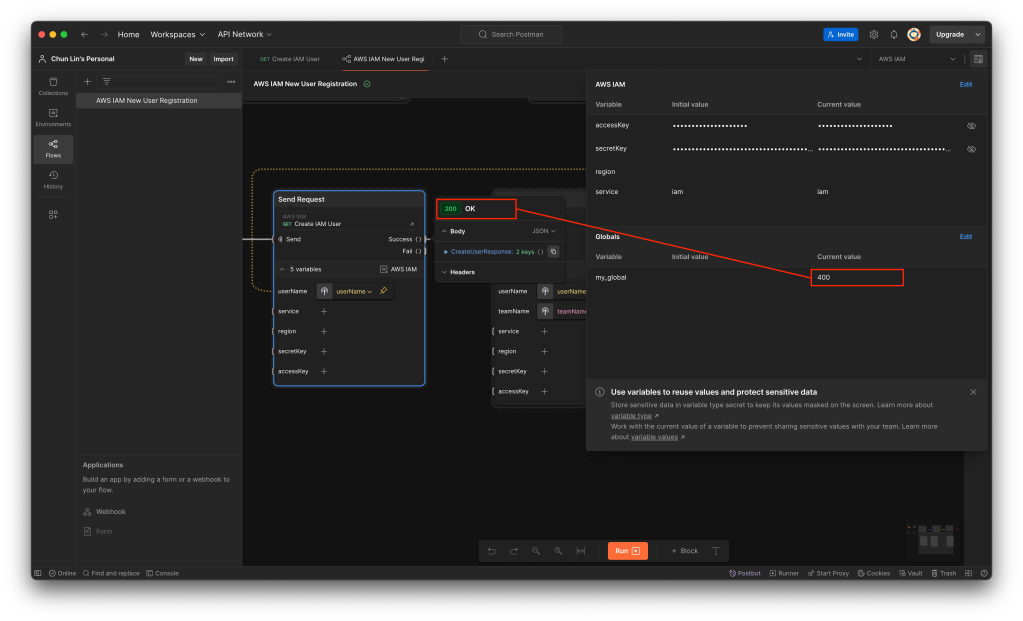
To do so, we need to update our request in the Collection. One of the snippets provided is actually about setting a global variable, so we can use it. For example, we add it to the post-response script of “Create IAM User” request, as shown in the screenshot below.

Let’s change the boilerplate code to be as follows.
pm.globals.set("my_global", pm.response.code);
Now, if we send a “Create IAM User” request, we will notice that a new global variable called my_global has been created, as demonstrated below.
However, now if we run our Flow, we will realise that my_global is not being updated even though the response code received is 200, as illustrated in the following screenshot.
Firstly, we need to understand that nothing is wrong with environments or variables. The reason why it did not work is because the variables just work differently in Flows from how they used to work in the Collection Runner or the Request Tab, as explained by Saswat Das, the creator of Postman Flows.
According to Saswat, global variables and environment variables are now treated as read-only values in the Flows, and any updates made to them through script are not respected.
So the answer to the question whether we can share variable across different Flows earlier is simply a big no by design currently.
Do It with CLI: Newman
Is there any alternative way that we can use instead of relying on the GUI of Postman?
Another teammate of mine from the QA team recently also showed how Newman, a command-line Collection Runner for Postman, can help.
A command-line Collection Runner is basically a tool that allows users to execute API requests defined in Postman collections directly from the command line. So, could we use Newman to do what we have done above with Postman Flows as well?
Before we can use Newman, we first need to export our Collection as well as the corresponding Environment. To do so, firstly, we click on the three dots (…) next to the collection name and select Export. Then, we choose the format (usually Collection v2.1 is recommended) and click Export. Secondly, we proceed to click on the three dots (…) next to the environment name and select Export as well.
Once we have the two exported files in the same folder, for example a folder canned “experiment.postman.newman”, we can run the following command.
$ newman run aws_iam.postman_collection.json -e aws_iam.postman_environment.json --env-var "userName=postman14462" --env-var "teamName=teamA" --env-var "groupName=testing-user-group"

While Newman and Postman Flows can both be used to automate API requests, they are tailored for different use cases: Newman is better suited for automated testing, integration into CI/CD pipelines, and command-line execution. Postman Flows, on the other hand, is ideal for visually designing the workflows and interactions between API calls.